All Blog Posts

Cyber Challenges and National Response: Pakistan’s Cybersecurity Review 2025
The year 2025 was a landmark year for cybersecurity awareness in Pakistan. Coordinated efforts by government agencies, semi-government institutions, telecom operators, academic institutions, private sector organizations, and digital platforms contributed to notable progress in digital safety and cyber resilience. Citizens and organizations were increasingly educated about online risks, safe digital behavior, and proactive cybersecurity practices. Cybersecurity Awareness Week 2025: A Nationwide Effort From December 11 to 17, 2025, the Pakistan Telecommunication Authority (PTA) led the nationwide Cybersecurity Awareness Week. This initiative brought together senior leadership from PTA and UNDP, representatives from PISA, PKCERT, telecom operators, academia, and the media to reinforce a unified commitment to digital safety and information integrity across the country. The event highlighted the importance of collaboration between public and private sectors to strengthen Pakistan’s overall cyber resilience. PKCERT and the Pakistan Information Security Framework 2025 One of the most significant milestones of 2025 was the release

PKCERT Introduces PISF 2025: A Strategic Step Toward National Cyber Security
At a time when cyber threats are growing in scale and sophistication, Pakistan has taken an important step by releasing the draft Pakistan Information Security Framework (PISF) 2025. The National Cyber Emergency Response Team (PKCERT) has played a key role in safeguarding Pakistan’s digital landscape, supporting national efforts to prevent, detect, and respond to cyber threats since its establishment. The PISF, developed by PKCERT, was opened for public review and consultation in late November and early December 2025. While it has not yet been formally launched as a finalized national policy, the consultation period concluded on December 4, 2025. Even in its draft form, PISF 2025 represents a major milestone, offering a clear and structured roadmap to strengthen information security across government organizations and critical national infrastructure. What is PISF 2025? PISF 2025 sets basic rules for keeping information safe in federal and provincial government offices, departments, independent groups, companies, CERTs, and key
Digital Trust Begins at Home: Securing Your Connected Life
Your home is more than walls and doors. Today, it is also your phone, your Wi-Fi, and the photos you share. One small mistake can let strangers into your life. A fake message can take your money. A photo posted by your child can show where you live. This guide is for every family in Pakistan. You don’t need to be a tech expert. Just follow simple steps to keep your home safe online. One Wi-Fi for All? That’s a Big Risk Most homes in Pakistan use just one Wi-Fi name and password. Your phone, your child’s tablet, the smart TV, and even the neighbor’s phone all connect to the same network. If one device gets a virus, it can spread to everything. A guest might download a fake app. Your child might click a “win free mobile” ad. Suddenly, your bank details are at risk. The fix is easy:

Mobilizing Communities for Digital Safety in Pakistan
Digital safety is no longer a topic for experts alone. In Pakistan, more people are going online every day, from urban centers to small towns and rural villages. Social media, online banking, messaging apps, and e-learning platforms have become part of everyday life. At the same time, risks such as online scams, misinformation, cyber harassment, and privacy violations are increasing. Raising awareness about these risks is important, but it is only the first step. Awareness alone does not protect people or change behavior. Communities need to move from awareness to practical action, equipping individuals with the knowledge and skills to navigate digital spaces safely. Mobilizing communities for digital safety means creating local networks where learning, discussion, and practical guidance happen on a regular basis. What Does Mobilizing Communities for Digital Safety Mean? Mobilizing communities for digital safety means people working together to learn, share, and help each other stay safe

NCCIA Pakistan: Safeguarding the Nation’s Digital Security
In today’s fast-paced digital world, where technology connects us like never before, the rise of cyber threats poses significant challenges to individuals, businesses, and national security. From online fraud and data breaches to cyberbullying and hacking, these threats can disrupt lives and economies. To tackle this growing concern, the Government of Pakistan established the National Cyber Crime Investigation Agency (NCCIA) in May 2024, a dedicated institution to protect the nation’s digital landscape. Operational since April 2025, the NCCIA has taken over the responsibilities previously managed by the Cyber Crime Wing of the Federal Investigation Agency (FIA). This article introduces the NCCIA, its mission, and how everyday Pakistanis can engage with it to report cybercrimes and contribute to a safer digital Pakistan. A Brief History: From FIA’s Cyber Crime Wing to NCCIA Before the NCCIA was formed, cybercrime investigations in Pakistan were handled by the Cyber Crime Wing of the Federal

It Starts With Us: Community-Led Learning for Safer Digital Lives
In an increasingly digital Pakistan, conversations around cybersecurity, misinformation, and online safety are no longer just technical concerns, they are everyday realities for millions. While policies and national strategies are essential, real change often begins at the grassroots level, in local communities where digital threats are most misunderstood and least addressed. There is a growing need for community-led capacity building that reaches people where they are. This means going beyond urban centers and into the underserved areas like small towns, rural communities, and low-income urban neighborhoods, where digital literacy levels remain low and internet use is growing fast. Instead of waiting for top-down programs to trickle in, we must start building knowledge and resilience from the ground up. A major step in this direction is to organize localized, accessible training workshops and awareness sessions. These community-based gatherings can help individuals understand critical topics like: Online scams and digital fraud Cyber

Stay Safe Online Amid Cyber Threats in Pakistan: Follow PKCERT Guidance
In light of recent tensions at the border and unusual online activity, our national cybersecurity team, PK CERT, is urging everyone to stay especially alert when using the internet. During times like these, misinformation can spread rapidly, and the risk of cyber threats increases. It’s particularly important not to share any photos or videos showing the movement of our armed forces, even if shared unintentionally, as they can be misused by those aiming to harm national security. By thinking carefully before clicking, sharing, or forwarding anything online, especially sensitive visuals, we can all play a part in protecting ourselves, our communities, and our country. Let’s stay responsible and support each other both online and offline. Here are some simple tips and guidelines: 1. Don’t Share Unverified Information Spreading unchecked news can cause unnecessary panic, damage trust in authorities, and help spread false narratives. Always verify content before sharing it. Avoid

2025 Cybersecurity Goals: Lessons from 2024 and Resolutions for a Safer Digital Future
As we approach the new year, it’s time to reflect on our digital habits and commit to better cybersecurity practices. Cyber threats are constantly evolving, and staying proactive is the key to protecting your personal and professional digital footprint. Here are some practical cybersecurity resolutions to help you secure your digital life in 2025. The Biggest Cybersecurity Lessons of 2024 Before diving into resolutions for 2025, let’s recap the key lessons from 2024 that shaped our understanding of cybersecurity: AI-Powered Threats on the Rise: The increasing use of AI in cyberattacks, such as AI-generated phishing scams, highlighted the need for advanced detection systems and user awareness. Supply Chain Vulnerabilities: High-profile breaches demonstrated the importance of securing not just direct systems but also third-party suppliers and vendors. Ransomware Evolution: Ransomware attacks became more sophisticated, targeting critical infrastructure and demanding higher ransoms. The lesson? Regular backups and incident response plans are crucial.
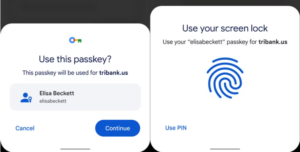
Your Passwords Are Outdated: Embrace Passkeys
Passwords have been the cornerstone of digital security for decades. But as cyberattacks become more sophisticated, relying on passwords alone is no longer enough to protect your online accounts. Weak, reused, and stolen passwords are among the most common entry points for hackers to access sensitive data. Fortunately, there’s a better alternative: passkeys. In this article, we’ll explore why traditional passwords are falling short, how passkeys work, and how they can safeguard your digital presence. Why Passwords Are No Longer Secure: Passwords have several inherent vulnerabilities: Weak and Reused Passwords: Many people create weak passwords or reuse them across multiple accounts, making them easy targets for hackers. Phishing Susceptibility: Hackers trick users into entering their passwords on malicious websites, gaining access to accounts effortlessly. Cybercriminals often trick users into revealing their passwords through phishing emails. Data Breaches: Large-scale data breaches can expose millions of passwords, leaving users vulnerable to identity theft

Why October is Cybersecurity Awareness Month: A Call to Action for Everyone
Introduction October is globally recognized as Cybersecurity Awareness Month, a time dedicated to raising awareness about the importance of cybersecurity and promoting best practices to ensure a safer digital world. This initiative is crucial in educating individuals, businesses, and institutions about the ever-evolving cyber threats and the necessary measures to protect against them. Headquarters and Administration: The initiative is spearheaded by the Cybersecurity and Infrastructure Security Agency (CISA), a component of the DHS, in partnership with the NCSA. These organizations provide resources, tools, and guidance to help individuals and businesses protect themselves from cyber threats. The headquarters for CISA is located in Washington, D.C., where strategic planning and coordination for the awareness month are conducted. The National Cyber Security Alliance (NCSA): A nonprofit organization focused on cybersecurity education and awareness. The U.S. Department of Homeland Security (DHS): A government agency responsible for national security, including cybersecurity. They launched the initiative in
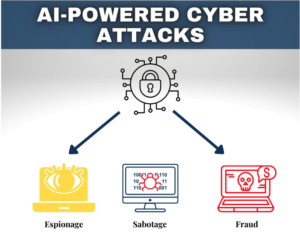
GPT-4 and AI-Generated Phishing: A New Era of Deception
In today’s digital age, we are constantly amazed by the power of artificial intelligence (AI). One such marvel is GPT-4, a highly advanced AI language model that can understand and generate human-like text. While this technology brings numerous benefits, it also has a dark side. Cybercriminals are now using AI, including models like GPT-4, to create more convincing and dangerous phishing attacks. This post will explore how AI is changing the landscape of online deception and what you can do to protect yourself. Understanding AI-Generated Phishing Phishing is a type of online scam where criminals try to trick you into giving away sensitive information like passwords or credit card numbers, etc. They often do this by pretending to be trustworthy organizations or individuals. Now, imagine these scammers equipped with AI that can write like a human. This is the new reality we are currently facing. AI-generated phishing takes traditional phishing

CrowdStrike Software Glitch: Global System Crash
A catastrophic global IT crisis unfolded on Friday, July 19, 2024, when a routine software update from cybersecurity giant CrowdStrike resulted in widespread system failures. Designed to bolster the Falcon sensor’s threat detection capabilities, the update inadvertently triggered a domino effect that paralyzed critical digital infrastructure across the globe. What actually happened? At 4:09 AM UTC on Friday, July 19, 2024, CrowdStrike initiated a standard update to its Falcon sensor for Windows systems. This update was designed to enhance the software’s ability to detect emerging cyber threats. However, a critical error within the Rapid Response component of the update caused widespread system failures. Windows devices running sensor version 7.11 and later, which were online between 4:09 AM and 5:27 AM UTC, were affected. CrowdStrike successfully reverted the faulty update at 5:27 AM UTC, halting the disruption. How Did It Happen? According to CrowdStrike’s Preliminary Post Incident Review (PIR) on July

Understanding Pakistan’s Cybercrime Legislation: PECA 2016 and the National Cyber Security Policy 2021
Pakistan has made significant strides in the domain of cyber legislation with the enactment of the Prevention of Electronic Crimes Act, 2016 (PECA 2016) and the National Cyber Security Policy 2021. These legislative frameworks aim to safeguard information systems, address cybercrime, and enhance information security across the nation. However, despite their ambitious goals, the effectiveness of these laws remains limited due to various implementation challenges, particularly in remote and underserved areas. This blog post scrutinize the key aspects of these legislations, their shortcomings, and practical recommendations for enhancing their effectiveness. PECA 2016: An Overview The Prevention of Electronic Crimes Act, 2016, was enacted to curb unauthorized activities related to information systems and to establish a legal framework for the investigation, prosecution, and trial of cybercrimes. Key provisions of PECA 2016 include: Unauthorized Access: Criminalizing unauthorized access to information systems. Data Damage: Penalizing data corruption or destruction. Electronic Fraud: Addressing various
Protect Your Privacy: Essential Tips for Safe App Installs on Smartphones
In our digital age, mobile applications have become an integral part of our daily lives, offering convenience and functionality at our fingertips. However, not all apps are created equal, especially when it comes to respecting your privacy. Whether you’re using an Android or an iPhone, it’s crucial to be vigilant about the apps you download and the permissions you grant them. Here are some best practices to ensure your privacy is protected when installing new apps. Recent Advisory from PKCERT Recently, PKCERT, our government institution, issued an advisory about certain matrimonial apps that collect and share personal data of users with third-party apps. This advisory highlights the importance of being cautious about the apps you download and the permissions you grant. For more detailed information, you can read the full advisory here. Best Practices for Safe App Downloads 1. Research Before You Download Before downloading any app, take the time

Empower Yourself Against Cybercrime: How to Report Incidents to FIA Cyber Wing
The internet connects us, informs us, and entertains us, but it also opens doors to cybercrime. If you’ve been a victim of online harassment, fraud, or any other cybercrime in Pakistan, the FIA Cyber Wing is there to help you fight back. Here’s a step-by-step guide on how to register and report your complaint: Reporting Options: The FIA Cyber Wing offers multiple ways to file your complaint: Online Complaint: Email Complaint In-Person Complaint Phone Complaint Online Complaint: This is the quickest and easiest option. Visit the FIA Complaint Registration Portal (https://fia.gov.pk/complaints_dept) and choose “Register Complaint” followed by “Cyber Crime Complaint.” Fill out the form meticulously, including: Full Name CNIC Contact Information Details Crime Category (Only one Crime Category option is available as selected in the screenshot). A clear description of the cybercrime (be specific!) Once all the required information is entered in the registration form, next step is enter Captcha and

Google Introduced VLOGGER
In the ever-evolving landscape of artificial intelligence, Google has once again pushed the boundaries of innovation with the introduction of Google Vlogger. This cutting-edge technology marks a significant leap forward in the realm of content creation, promising to revolutionize the way we produce and consume video content. What is Google Vlogger? Google Vlogger is an advanced AI-powered platform designed to assist creators in generating high-quality video content effortlessly. Leveraging state-of-the-art machine learning algorithms, Google Vlogger empowers users to create engaging videos with minimal time and effort. How Does it Work? At the core of Google Vlogger lies a sophisticated neural network trained on vast amounts of video data. By analyzing patterns, styles, and trends in existing content, the AI engine can generate custom-tailored video content based on user input and preferences. Users simply provide Google Vlogger with a brief outline or script, along with any specific instructions or preferences, and

Professor Dr. Haider Abbas Honored with Tamgha-i-Imtiaz
On a momentous occasion on the 23rd of March 2024, Professor Dr. Haider Abbas was bestowed with the highest civil honor ‘Tamgha-i-Imtiaz’ by the Government of Pakistan. This award recognizes his exceptional contributions to the field, marking a significant moment in his esteemed career. Dr. Abbas has long been hailed as a leader in cybersecurity, known for his dedication to advancing knowledge and inspiring others in the field. His pioneering research and visionary leadership have earned him acclaim both at home and around the globe. Leading Innovations at the Forefront Professor Dr. Haider Abbas has long been recognized as a pioneer in the field of cybersecurity. His relentless pursuit of excellence and unwavering commitment to advancing the boundaries of knowledge have earned him widespread acclaim both nationally and internationally. Through his groundbreaking research and visionary leadership, he has emerged as a guiding light for aspiring cybersecurity professionals worldwide. Unmatched Contributions

Guide to Outsmarting Social Engineering Scams
Imagine you’re browsing the web when suddenly, a message pops up offering a free iPhone! Wow, right? But before you start celebrating, let’s hold on a sec. This could be a trap set by a tricky online con artist using a sneaky tactic called social engineering. What’s social engineering? Think of it as the digital version of a pickpocket at a crowded market. Instead of stealing wallets, these cyber tricksters use smooth talk and clever tricks to steal your secret information or make you do things that put you at risk online. Don’t worry, though! In this post, we’ll become internet detectives and uncover the secrets of social engineering scams. We’ll learn about the tricks these online tricksters use and how to spot them before it’s too late. Let’s unmask some common social engineering scams: Phishing: Phishing is like a trick where bad guys pretend to be someone you trust

Learning Essential Cybersecurity Terminologies
In the world of digital security, understanding key terms and concepts is crucial for keeping organizations and individuals safe from ever-evolving online threats. Let’s dive into some fundamental ideas that empower security professionals to identify and tackle potential dangers, all while keeping things simple and easy to grasp. Playing by the Rules: Compliance Think of compliance as following the rules—both inside and outside the organization. It’s about sticking to the guidelines set internally and meeting external regulations to avoid legal troubles and security breaches. Basically, it’s the digital version of making sure everyone is on the same page. Fortifying Defenses: Security Architecture Think of security architecture as the blueprint for our digital fortress. It’s a design made up of different tools and processes that work together to shield an organization from risks and outside threats. Picture it as the master plan for keeping the digital castle safe and secure. Putting
Understanding Penetration Testing
Imagine a practice cyberattack against your computer system. That’s essentially what penetration testing, or pen testing for short, is. It’s like a controlled experiment where security experts, known as pen testers, attempt to find weaknesses in your system using the same tools and techniques as real attackers. This process helps identify any vulnerabilities before malicious actors can exploit them, ensuring your data remains safe. Why is it important? Think of it like checking your house for leaks before the rain comes. Pen testing is crucial because it helps you proactively identify and address security weaknesses in your systems before hackers have a chance to exploit them. This can prevent data breaches, financial losses, reputational damage, and other negative consequences. How does it work? Pen testers essentially act like ethical hackers. They use various tools and techniques, such as vulnerability scanners, social engineering, and code injection, to mimic real-world attacks. By

Disproving Common Cybersecurity Misconceptions
In the digital age, where cybersecurity is a buzzword, misinformation often abounds. To navigate the complex landscape of cyber threats, it’s crucial to separate fact from fiction. Join us on a journey as we debunk common cybersecurity myths, enhance awareness, and fortify our defenses against evolving trends in the cyber realm. Myth 1: Cybersecurity is Only for Big Companies One prevalent misconception is that cybersecurity is solely the concern of large corporations. In reality, cyber threats spare no one. Small businesses and individuals are equally susceptible. Recent trends show a surge in cyberattacks targeting smaller entities as cybercriminals exploit potential vulnerabilities. Prioritize cybersecurity, regardless of the scale of your digital presence. Myth 2: Strong Passwords Are Enough to Protect Against Cyber Threats While strong passwords are a fundamental aspect of cybersecurity, relying solely on them is a myth. Cyber threats evolve, and sophisticated attack methods such as phishing and social

Bouncing Back from a Cybersecurity Incident
In today’s hyperconnected world, where every device is a potential gateway, cybersecurity incidents are an ever-present threat. When the inevitable occurs, having a robust recovery plan is your lifeline. This comprehensive guide will illuminate the path to regaining your digital footing, addressing key steps and industry trends. Embark on this journey with us as we rebuild your resilience in the face of cyber threats. Why Cybersecurity Recovery Matters: The sophistication of cyber threats is constantly evolving, demanding a comprehensive recovery strategy. Recent data reveals a surge in cyberattacks, with incidents skyrocketing by a staggering 55% in the past year alone. Navigating the aftermath of a breach requires a strategic and informed approach. Imagine waking up to the news that your company’s sensitive customer data has been compromised due to a sophisticated ransomware attack. The implications are far-reaching, potentially leading to financial losses, reputational damage, and legal repercussions. Without a well-defined

Overcoming Cyberattacks and Learning from Experience
In the ever-expanding digital realm, cyberattacks have emerged as a formidable threat, posing significant risks to individuals, organizations, and even nations. These attacks can wreak havoc, causing financial losses, operational disruptions, and reputational damage. Yet, amidst these challenges, there are also inspiring stories of resilience and adaptation. Organizations and individuals worldwide are learning from their experiences and implementing strategies to protect themselves from cyber threats, emerging stronger and more resilient. 1. Target Breach: A Wake-Up Call for Data Security In 2013, Target, a major American retailer, suffered a massive data breach that exposed the personal information of millions of customers. This incident served as a stark reminder of the vulnerabilities of our data and the importance of robust cybersecurity measures. Hackers infiltrated Target’s systems, gaining access to sensitive customer data, including names, addresses, and credit card information. This breach exposed the personal details of over 70 million customers, causing widespread

Navigating Social Media Securely and Responsibly
In our digital age, social media is the heartbeat of our online connections. However, the convenience of sharing our lives comes with the responsibility of protecting our privacy and personal data. Let’s dive into some practical tips, backed by real-world examples and crucial statistics, to help you navigate social media securely: 1. Review Your Privacy Settings: Take a moment to delve into the privacy settings of your social media accounts. Adjust who can see your posts, friend requests, and personal information to match your comfort level. On Instagram, you can set your account to private, allowing only approved followers to see your posts and stories. Shockingly, 79% of users have at least one social media account with inadequate privacy settings. Regularly reviewing and adjusting your settings is vital for online security. 2. Think Before You Share: Be mindful of the information you share online. Avoid oversharing personal details, such as

Shopping Safely Online and Avoiding Scams
Embarking on a digital shopping spree can be exciting, but it’s essential to navigate the online marketplace with caution. Protecting your personal information and avoiding scams is crucial to ensuring a safe and enjoyable online shopping experience. Let’s explore practical tips, backed by examples and statistics, to help you shop securely: 1. Shop from Trusted Websites: When making online purchases, stick to well-known and reputable websites. Trusted platforms have secure payment systems and robust measures in place to protect your information. Opt for established e-commerce giants like Amazon or recognized brands’ official websites when buying products online. 56% of online shoppers prefer to shop from well-known retailers due to trust and security concerns, indicating the importance of choosing reliable platforms. 2. Check for Secure Website Connections: Before entering any personal information or payment details, ensure the website is secure. Look for “https://” in the URL and a padlock icon in

Keeping Your Children Safe Online
In the modern digital age, children are navigating the online world from a young age. While the internet offers incredible opportunities, it also presents potential risks. As parents, fostering digital responsibility is crucial to ensure your children’s safety online. Here are practical tips, examples, and statistics to guide you in this important endeavor: 1. Open Communication is Key: Communication lays the foundation for digital responsibility. Keep an open dialogue with your children about their online activities, friends, and experiences. Regularly discuss online content with your child. Ask about their favorite websites, games, or videos, fostering a comfortable space for them to share. 67% of children are more likely to report feeling bothered by something online if they have a trusting relationship with their parents. Open communication promotes a safer digital environment. 2. Set Clear Online Rules and Boundaries: Establishing rules helps your child understand the importance of responsible online behavior.

Shielding Your Smartphone from Cybersecurity Threats
In the palm of your hand rests a powerful tool, your smartphone, connecting you to the digital world. However, with great convenience comes the responsibility of safeguarding your device from cyber threats. Let’s explore practical tips to shield your smartphone and personal data from potential security breaches: 1. Lock Your Device with a Strong Password or PIN: Your smartphone is like a digital diary, holding valuable information. Set a robust password or PIN to keep unauthorized users at bay. Instead of using common PINs like “1234,” opt for a combination that includes numbers, letters, and symbols for added security. 30% of smartphone users do not secure their devices with a password or PIN, making it easy for unauthorized access. 2. Keep Software and Apps Updated: Regularly updating your smartphone’s operating system and apps is like adding a layer of armor. Updates often contain security patches, closing vulnerabilities that hackers may

A Guide to Secure Your Home Wi-Fi Network
In the realm of digital connectivity, your home Wi-Fi network is the castle that guards your online kingdom. Just as you wouldn’t leave the doors to your house wide open, securing your Wi-Fi is essential to prevent unwanted guests and ensure a safe digital environment. Let’s delve into practical tips to fortify your home Wi-Fi network against potential threats: 1. Set a Strong Wi-Fi Password: Creating a robust password for your Wi-Fi is like installing a sturdy lock on your front door. Make it a combination of letters, numbers, and symbols to discourage unauthorized access. Avoid using easily guessable passwords like “password123.” Instead, opt for something unique and challenging, such as “B1gD!git@lF0rtress.” 81% of successful breaches occur due to weak or stolen passwords. Strengthening your Wi-Fi password significantly reduces the risk of unauthorized entry. 2. Change Default Router Credentials: Just as you wouldn’t keep your house key under the doormat,

Phishing Scams: Safeguarding Your Information
Imagine the internet as a huge sea full of tricky predators called phishing scams. They want to fool you into giving away important information. But don’t worry! If you learn about these scams and take simple steps to be careful, it’s like putting on armor to protect yourself from their tricks in the digital world. 1. Understanding Phishing: Phishing, a digital deception, occurs when scammers impersonate trustworthy entities. For instance, imagine receiving an email urgently requesting your bank login credentials. An email claiming to be from your bank might state that there’s been unauthorized activity on your account, prompting you to click a link and enter your details. 97% of people globally struggle to identify sophisticated phishing emails, emphasizing the need for awareness and caution. 2. Recognizing Red Flags: Identifying phishing attempts involves spotting signs like generic greetings or spelling errors. Legitimate entities won’t request sensitive information via email. A

Antivirus Software: Your Shield Against Digital Threats
In our digital age, where our lives are intricately woven with technology, having a reliable shield against online threats is crucial. Enter antivirus software—your digital guardian. Let’s explore the importance of antivirus protection in simple terms, backed by real-world examples and essential statistics. 1. The Digital Jungle and Its Dangers: The internet, like a bustling jungle, is filled with hidden dangers. According to recent statistics, there’s a new malware threat every 4.2 seconds. These threats come in various forms, from viruses that can corrupt your files to phishing attempts aiming to steal your personal information. 2. What’s Antivirus Software, Anyway? Think of antivirus software as the immune system for your computer. It’s designed to detect, prevent, and remove malicious software, just like how your body fights off infections. For example, if you unknowingly download a file containing a virus, your antivirus software steps in to neutralize the threat before it

Social Media Privacy Settings with Confidence
Welcome to the digital era, where social media is our virtual playground. As we share, connect, and explore, it’s crucial to understand the ins and outs of social media privacy settings. Let’s embark on a journey to navigate the digital landscape with confidence, ensuring your online world remains private and secure. 1. Why Social Media Privacy Matters: In a world where oversharing is the norm, safeguarding your personal information is vital. According to recent statistics, over 80% of social media users have concerns about their privacy online. Your data is like a digital fingerprint; let’s make sure it’s protected. For instance, consider how much you’re comfortable sharing publicly and reassess your privacy settings accordingly. 2. Review and Update Your Settings: Take a stroll through your social media privacy settings. Platforms like Facebook, Instagram, and Twitter have specific settings that allow you to control who sees your posts, who can send

A Step-by-Step Guide to Protecting Your Digital Life
In our digital age, where everything is just a click away, securing your online life is paramount. Let’s embark on a journey to fortify your digital defense by crafting strong passwords. Here’s a step-by-step guide with practical examples to ensure your online world remains safe. Understanding the Cybersecurity Need: Cybersecurity acts as a digital bodyguard, ensuring your online information stays safe. Avoid using overly simple passwords like “password” or “123456”; they’re akin to leaving your front door wide open for cyber trouble. Creating Strong Passwords: Aim for passwords that are a minimum of 12 characters long. Mix it up with a combination of upper- and lower-case letters, numbers, and symbols. For instance, transform “password123” into a robust code like “P@ssw0rd#123.” Complexity makes it significantly harder for cyberattackers to crack your password. Avoiding Easy-Peasy Passwords: Steer clear of using personal information such as your birthday or common words. Each account deserves

CyberWalk: Your Gateway to Cybersecurity Empowerment
Welcome aboard, cyber enthusiasts! Whether you’re a tech wizard or a complete novice, CyberWalk is here to guide you on a journey through the fascinating world of cybersecurity. In this digital age, where technology intertwines with every aspect of our lives, understanding and securing our online presence is more crucial than ever. Step into CyberWalk, where we not only unravel the complexities of cybersecurity but also foster a community of digital explorers. Together, we’ll navigate the ever-evolving cyber landscape, ensuring you’re not just secure but empowered in the digital realm. Why Cybersecurity Matters Think of cybersecurity as the digital guardian that protects your online kingdom. From personal data to financial transactions, we leave digital footprints everywhere. Without proper protection, these footprints become vulnerable to cyber threats. Cybersecurity is not just for big corporations; it’s for every individual navigating the web. In a world where our lives seamlessly blend with the

CyberWalk: A Mission to Empower Digital Citizens
Greetings, digital explorers! Today marks the dawn of a new era in your online journey as we introduce CyberWalk—a platform with a mission to empower and guide digital citizens through the intricate landscapes of the digital world. In this guide, we’ll walk you through the essence of CyberWalk and provide step-by-step guidance on how to embark on this empowering journey. Step 1: Understanding the CyberWalk Mission At the heart of CyberWalk lies a commitment to empower digital citizens with knowledge. In a rapidly evolving digital landscape, understanding the fundamentals of cybersecurity is no longer a luxury but a necessity. Our mission is clear: to make cybersecurity accessible, understandable, and applicable to everyone. Think of CyberWalk as your digital guide, a trustworthy companion on your journey through the complexities of the online realm. Our mission is to provide you with the tools and knowledge to navigate this digital landscape confidently. Step

The Fundamentals of Cybersecurity
Welcome, digital pioneers! In the vast landscape of the internet, where data flows like a digital river, ensuring your safety is paramount. Cybersecurity is your shield against the ever-evolving threats that lurk in the digital shadows. In this primer, we’ll delve into the fundamentals of cybersecurity, breaking down complex concepts into actionable insights to fortify your digital defenses. Understanding the Basics At its core, cybersecurity is the practice of safeguarding digital systems, networks, and data from unauthorized access, attacks, and damage. It’s the virtual lock and key that keeps your digital world secure. Just as you lock your front door to protect your home, cybersecurity locks down your digital presence. It prevents unauthorized users from entering and safeguards your digital valuables. The CIA Triad Confidentiality: Ensuring that only authorized individuals can access sensitive information. Integrity: Maintaining the accuracy and reliability of data throughout its lifecycle. Availability: Guaranteeing timely and reliable access to data
Let's connect
- +92-333-5923709
- hello@cyberwalk.pk
- Software Technology Park, I-9, Islamabad, ICT 44000
